Introduction
Every digital action leaves behind a footprint. Whether it’s creating a document, visiting a website, connecting a USB device, or sending an email, systems silently record timestamps and activity logs. For forensic experts, these traces are more than scattered fragments; they are pieces of a story waiting to be told.
Timeline analysis in digital forensics is the art and science of arranging digital events in chronological order to reconstruct what happened, when it happened, and sometimes even how it happened. It transforms raw data into a narrative, helping investigators uncover hidden truths in both cybercrimes and civil disputes.
This blog explores what timeline analysis is, its techniques, tools, challenges, and why it is an indispensable process in digital forensics.
What is Timeline Analysis?
Timeline analysis is the process of reconstructing a sequence of events from digital artefacts. Investigators collect, sort, and analyse data to create a chronological view of user activities or system events.
For instance, in a case of suspected data theft from a company, timeline analysis can reveal:
-
When an employee logged into the system.
-
Which files were accessed, modified, or copied?
-
If an external device (USB) was connected.
-
When the files were deleted or transferred.
This step-by-step reconstruction provides clarity to investigators and solid evidence for court proceedings.
Key Sources of Timeline Data
Digital devices generate data in many forms. Some of the most valuable sources for timeline analysis include:
-
File Metadata (MAC Times)
-
MAC stands for Modified, Accessed, and Created times.
-
These timestamps help determine when a file was edited, viewed, or generated.
-
Operating System Logs
-
Windows Event Logs, Linux syslogs, and macOS Unified Logs track system activities such as logins, errors, and shutdowns.
-
Registry and System Configuration Files
-
In Windows, registry entries reveal the dates of software installations, the last-used applications, and user activities.
-
Web Browsing History
-
Communication Records
-
Emails, chat applications, and VoIP logs reveal when messages were sent, received, or deleted.
-
Application Logs
-
External Devices and Media
By correlating these diverse sources, investigators can create an accurate picture of digital activity.
Techniques in Timeline Analysis
Timeline analysis involves multiple methods depending on case requirements:
-
Manual Review
-
Investigators manually examine logs, files, and timestamps.
-
Useful for small datasets but time-intensive for large-scale investigations.
-
Automated Timeline Construction
-
Correlation of Events
-
Different sources are compared to validate findings.
-
Example: If a file was copied at 11:30 AM, investigators check whether a USB was connected at the same time.
-
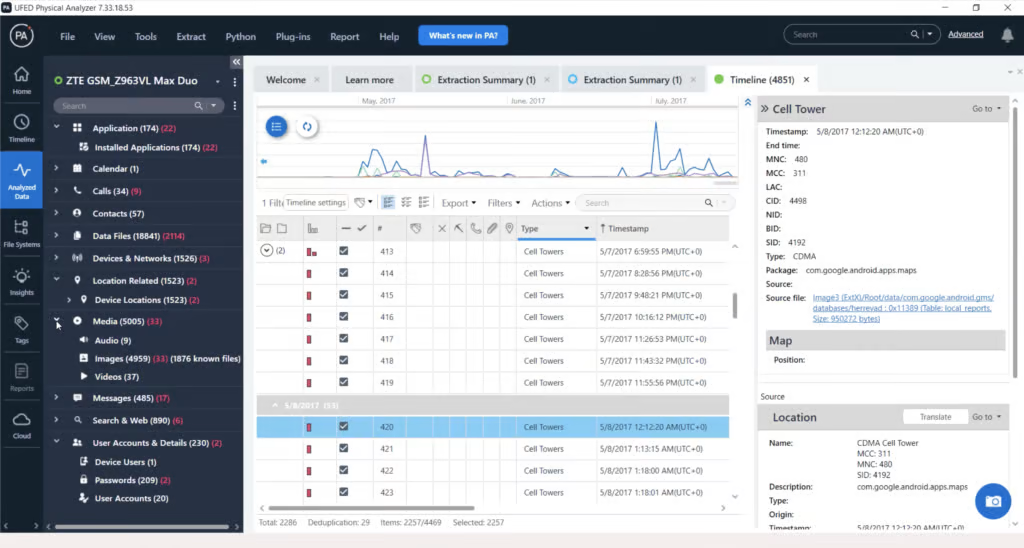
Visualization
Popular Tools for Timeline Analysis
Several tools assist forensic experts in creating and analysing timelines:
-
Plaso / log2timeline
-
The Sleuth Kit & Autopsy
-
X-Ways Forensics
-
Forensic Toolkit (FTK)
-
Magnet AXIOM
Each tool has unique strengths, and often investigators use multiple tools for cross-verification.
Real-World Applications of Timeline Analysis
Timeline analysis finds applications across different types of investigations:
-
Cybercrime Investigations
-
Fraud and Insider Threats
-
Data Breach Cases
-
Civil Litigation
-
Accident and Incident Reconstruction
In short, timeline analysis acts as a forensic storyteller—turning scattered fragments of digital evidence into a logical sequence of events.
Challenges in Timeline Analysis
Despite its importance, timeline analysis comes with its own set of challenges:
-
Overwhelming Volume of Data
-
Timestamp Manipulation
-
Time Zone Differences
-
Volatile Data Loss
-
Anti-Forensic Techniques
Overcoming these challenges requires advanced tools, expertise, and meticulous methodologies.
Best Practices for Effective Timeline Analysis
To ensure accuracy and reliability, forensic experts follow best practices such as:
Conclusion
Timeline analysis is one of the most powerful methods in digital forensics. By connecting scattered data points into a chronological sequence, investigators can reconstruct events with clarity and precision.
Whether it’s a case of cybercrime, data theft, fraud, or even accident reconstruction, timeline analysis uncovers the who, what, when, and how of digital activities.
In today’s digital age, where every click and keystroke matters, mastering timeline analysis is no longer optional—it is essential for investigators, cybersecurity experts, and legal professionals seeking the truth.



Post comments (0)