Different Types Of Smartphone Security Explained
-
Password lock
It is one of the most secure methods of smartphone protection. It requires the user to enter a custom alphanumeric password (letters, numbers, symbols) to access the device.
Best for: Professionals and users storing sensitive data on their phones who prioritize maximum security.

-
Fingerprint lock
Uses your biometric fingerprint data for secure and quick access. Reliable and widely used.
Best for: Everyday users who want a secure and quick way to access their phones with minimal effort.

-
Face lock
Facial recognition scans your face to unlock the phone. Fast and hands-free, though less secure on some models.
Best for: Users who value convenience and quick access, especially on modern smartphones with advanced facial recognition.

-
Smart Lock
Keeps your phone unlocked in trusted conditions (e.g., home, connected device). Offers convenience with moderate security.
Best for: Users who want a convenient unlock method at home or in a controlled environment.

-
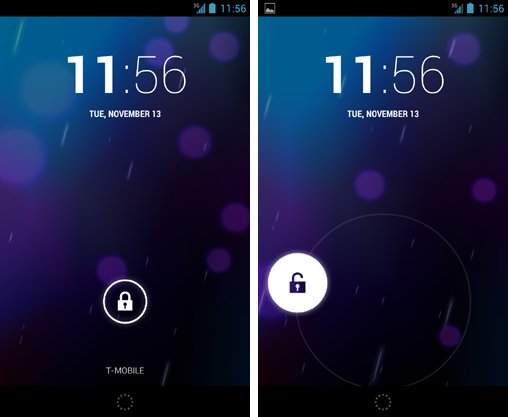
Swipe
Simple screen swipe to unlock. Easy but offers no real security—suitable only for minimal protection.
Best for: Non-personal or demo devices with no sensitive data (not recommended for daily use).

-
Pattern Unlock
Draw a specific pattern on a grid. Easier to remember than a password, but can be guessed from smudge trails.
Best for: Users who prefer visual memory and want moderate security without typing.

-
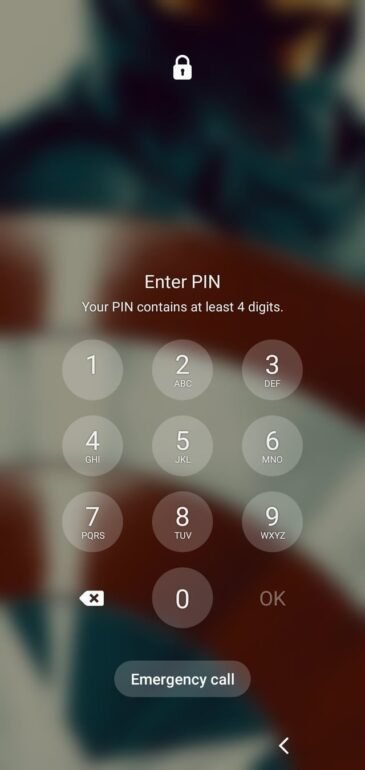
PIN Lock
Uses a 4 to 6-digit numeric code. Simple yet secure if not easily guessable.
Best for: Users who want a balance of speed and security for daily use.

Which Smartphone Security Option Is Right for You?
| Security Type |
Security Level |
Convenience |
Recommended Use |
| Password Unlock |
🔒🔒🔒🔒🔒 |
😐 |
High-security users |
| Fingerprint Unlock |
🔒🔒🔒🔒 |
😄 |
Everyday use |
| Face Unlock |
🔒🔒🔒 |
😄 |
Fast, hands-free unlock |
| Smart Lock |
🔒🔒 |
😍 |
Trusted locations |
| Swipe Unlock |
❌ |
😍 |
Not recommended |
| Pattern Unlock |
🔒🔒 |
🙂 |
Light-medium security |
| PIN Lock |
🔒🔒🔒 |
🙂 |
General security |
Smartphone Security in Digital Forensics
In digital forensics, bypassing lock methods is a major part of data extraction. Tools like Cellebrite, Magnet AXIOM, and Oxygen Forensics are often used to:
Understanding lock mechanisms helps forensic experts determine which tools or techniques are required in investigations.
Final Thoughts
Choosing the right smartphone security depends on your needs. While biometrics and PINs offer a good balance of security and convenience, it’s crucial to avoid insecure methods like swipe unlock or simple patterns.
Always update your phone, enable biometric and two-factor authentication, and use trusted apps only.
Need Help with Smartphone Data Recovery or Forensics?
At Hawk Eye Forensic, we offer:
-
Mobile Data Recovery Services
-
Smartphone Forensics (Android & iOS)
-
Digital Investigations and Evidence Extraction
-
Advanced Tools like JTAG, Chip-off & Logical Extraction
🔗 Visit us: www.hawkeyeforensic.com
📞 Call: +91-9718888589
#SmartphoneSecurity #MobileForensics #AndroidSecurity #FaceUnlock #FingerprintSecurity #DigitalForensics #CyberSecurity #PhoneUnlock #DataProtection #HawkEyeForensic










Post comments (0)