Encryption and its impact on Digital Forensic
In the digital age, encryption has become an integral part of our daily lives, serving as a crucial tool for securing sensitive information and protecting our privacy. But the increasing ...


Digital Forensics Anjali Singhal todayApril 3, 2024

When it comes to digital forensics, the imaging process is one of the most important steps in collecting and preserving evidence. There are many different methods that experts use to replicate digital storage media, and each has its own advantages and disadvantages.
One of the most common methods for forensic imaging is known as “bit-stream copying.” With this method, the entire contents of a storage device are copied onto another storage device, bit by bit. This ensures that all data on the original storage device is captured, including any hidden or deleted files.
A hash value, also known as a checksum or digital fingerprint, is a unique alphanumeric string generated by applying a cryptographic hash function to data. In the context of forensic imaging, hash values serve as digital signatures that verify the integrity and authenticity of disk images. By comparing the hash values of the original drive and its image, investigators can ensure that the data remains unaltered and untampered during the imaging process.
Consistency in hash values is crucial for maintaining the credibility and admissibility of forensic evidence in legal proceedings. When multiple forensic tools produce identical hash values for the same disk image, it strengthens the reliability and accuracy of the evidence. Consistent hash values provide assurance that the image has not been tampered with or altered in any way, bolstering the integrity of the investigative process.
Employing multiple forensic tools in the imaging process helps mitigate the risk of errors and discrepancies that may arise from using a single tool. Each tool utilizes different algorithms and methodologies for generating hash values, enhancing the robustness and reliability of the verification process. By cross-referencing hash values obtained from different tools, investigators can detect inconsistencies and ensure the accuracy of the imaging process.
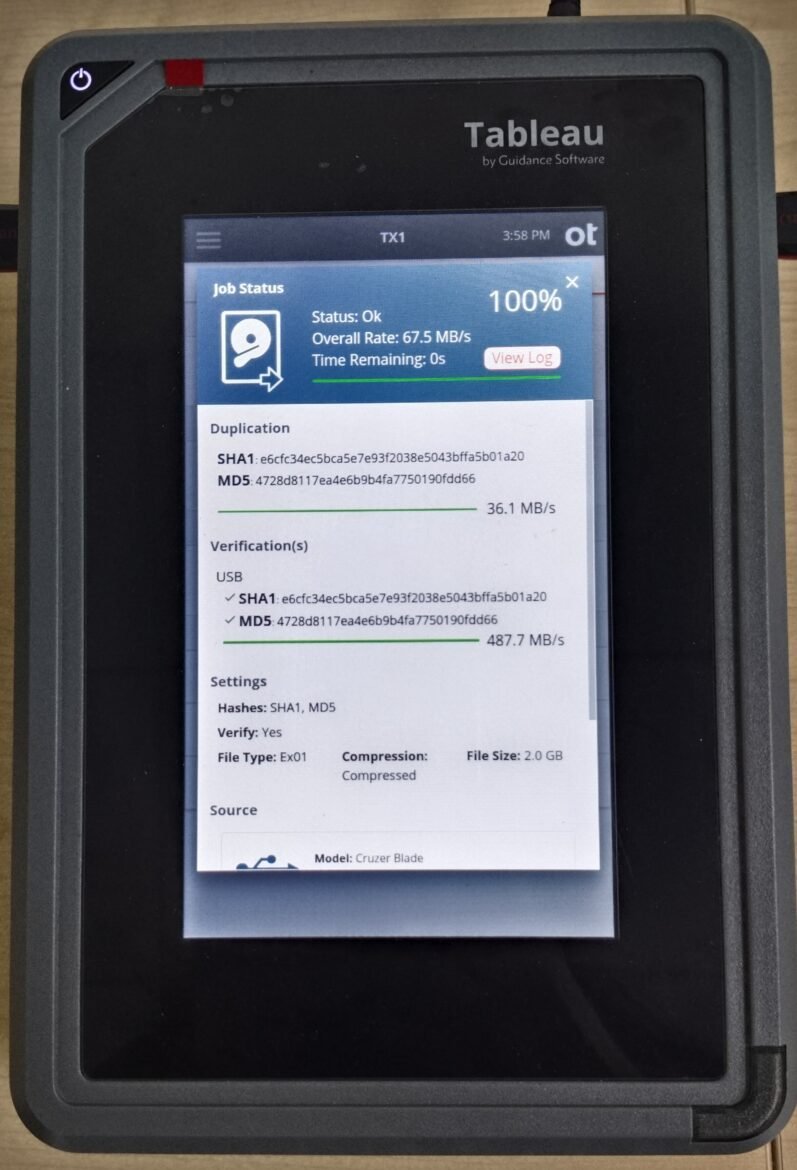
Image 1: Showing Hash Value by Tableau TX1
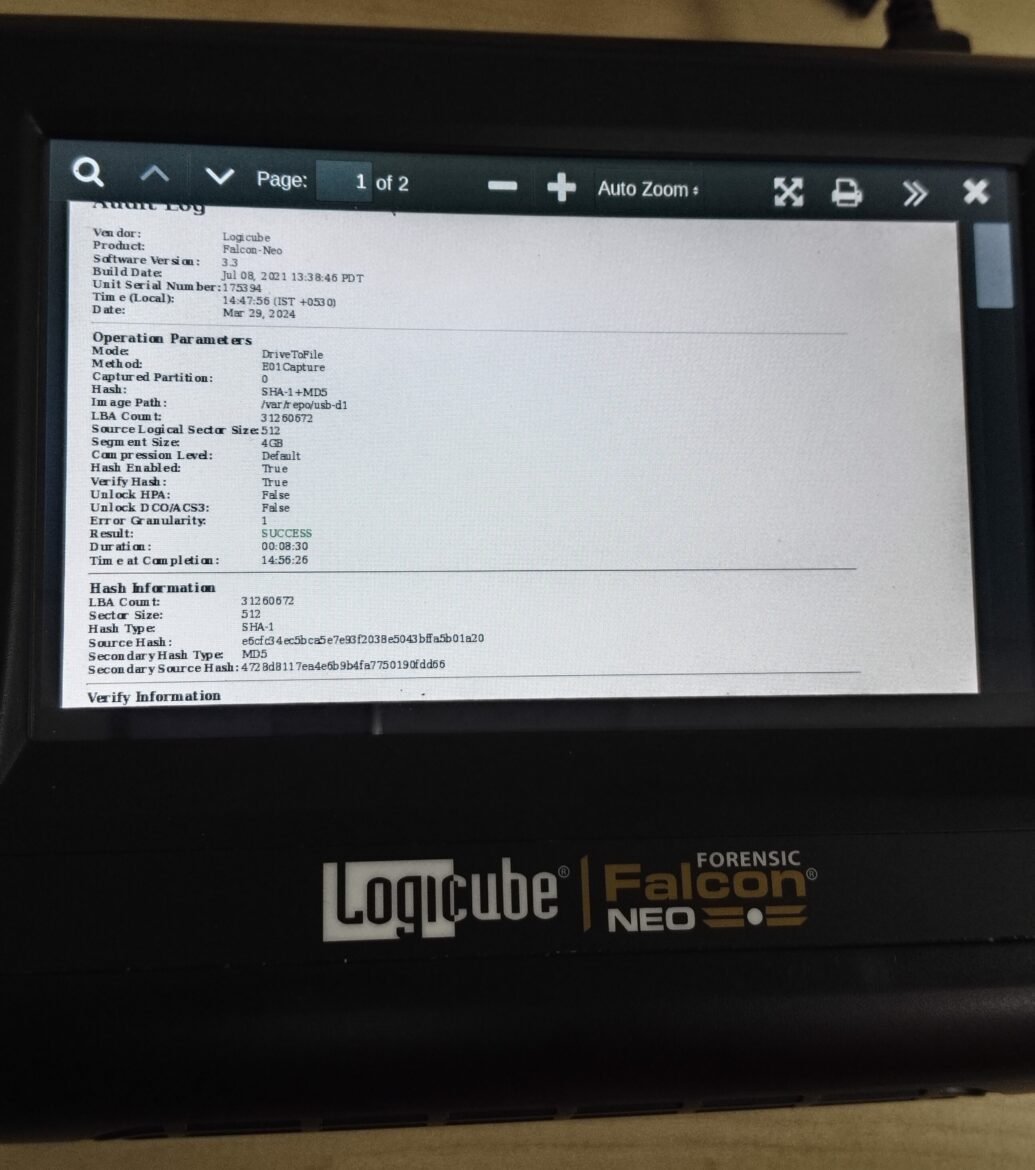
Image 2: Showing Hash Value by Logicube Falcon NEO
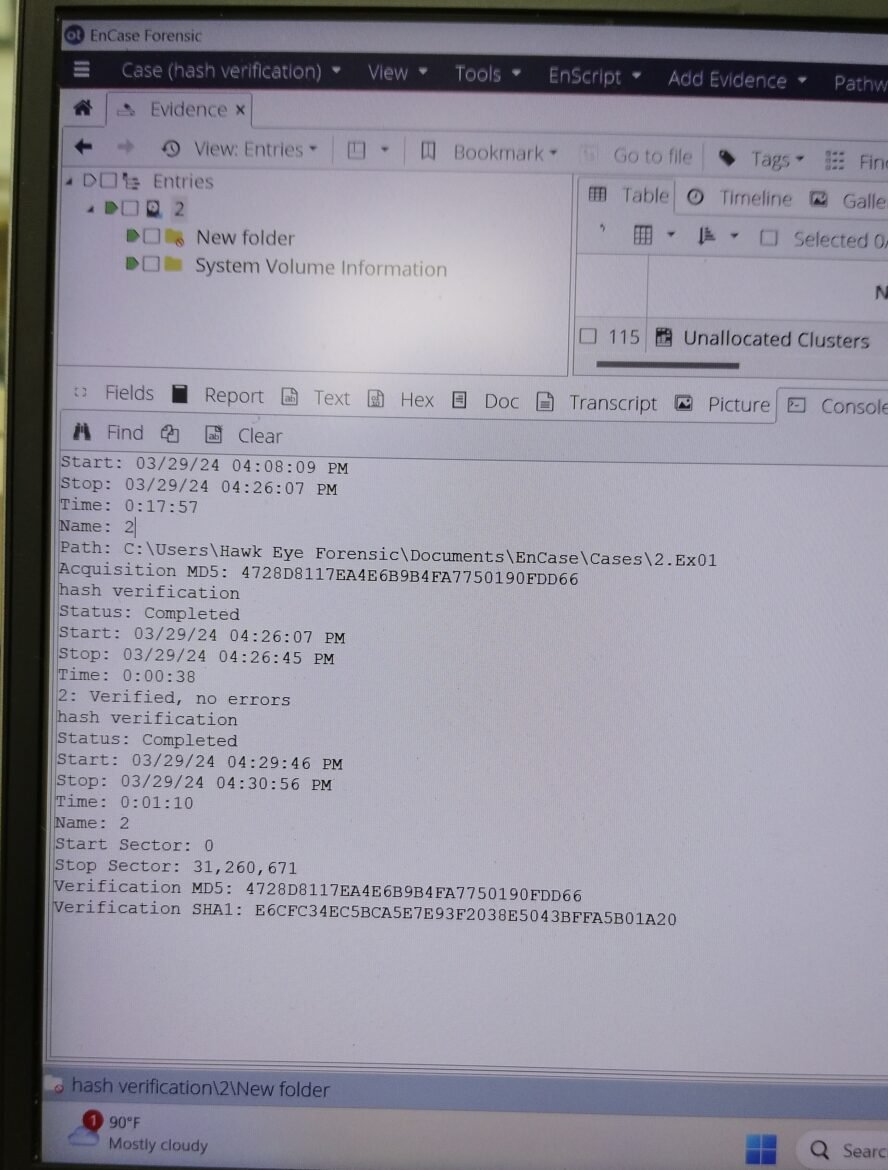
Image 3: Showing Hash Value by EnCase Forensic
The above images indicates that all 3 forensic tools i.e. (Tableau TX1, Logicube Falcon NEO and EnCase Forensic) are providing the same hash values when creating a forensic image of a drive.
To maintain consistent hash values during hard drive imaging, forensic examiners should adhere to best practices:
Use Trusted Forensic Tools: Select reputable forensic imaging tools that are widely recognized and validated within the digital forensics community. Tools such as EnCase Forensic, FTK Imager, and X-Ways Forensics are commonly used for disk imaging and hash verification.
Verify Hash Values Across Multiple Tools: After creating a disk image, verify its hash value using multiple forensic tools to confirm consistency. Cross-referencing hash values obtained from different tools adds an extra layer of validation and reduces the risk of false positives or discrepancies.
Document Imaging Procedures: Maintain detailed documentation of the imaging process, including the tools used, parameters configured, and hash values generated. This documentation serves as a record of the investigation’s integrity and can be presented as evidence in legal proceedings.
Implement Chain of Custody Protocols: Establish strict chain of custody protocols to track the handling and transfer of disk images throughout the investigation. Documenting each step of the imaging process and maintaining a clear audit trail helps preserve the integrity and admissibility of forensic evidence.
In digital forensics, ensuring the integrity and authenticity of evidence is essential for conducting thorough and reliable investigations. By employing multiple forensic tools that produce consistent hash values during hard drive imaging, investigators can enhance the credibility and reliability of forensic evidence. Adhering to best practices and maintaining meticulous documentation throughout the imaging process is critical for upholding the integrity of forensic investigations and ensuring the admissibility of evidence in legal proceedings.
Reach out to us any time to get customized forensics solutions to fit your needs. Check out Our Google Reviews for a better understanding of our services.
If you are looking for Forensics Imaging Services in Delhi/NCR, give us a call on +91 9289459589.
Written by: Anjali Singhal
Tagged as: Data Acquisition, CRC32, Chain of Custody, Data Preservation, Data validation, Forensic Tools, Evidence handling, verification, Forensic Imaging, Imaging process, Authentication, Hash Values, Verification process, Data Integrity, SHA-1, Anti-tampering measures, MD5, SHA-256, Read-only access, Digital forensics, Hash Algorithms, Data duplication, Digital evidence, Drive imaging, Data security, Consistency, Disk imaging, File integrity.

In the digital age, encryption has become an integral part of our daily lives, serving as a crucial tool for securing sensitive information and protecting our privacy. But the increasing ...

Copyright 2016-2025 all rights reserved by Hawk Eye Forensic.
Post comments (0)