
PITFALLS OF USING A VPN
Virtual private networks (VPNs) have increased in popularity in recent years as more people look to protect their online privacy and security. A VPN encrypts your internet traffic and routes ...


Server Side Request Forgery (SSRF) is a type of cyber attack, it is a web application vulnerability that has recently gained attention due to its potential for devastating consequences. In this malicious actors exploit vulnerabilities in web applications using this attack vector, manipulating user-supplied input to create requests on the server side and access internal resources or systems with the server’s trusted network privileges.
In this blog post, we will look into the complexities of SSRF, its impact, and the best practices for mitigating this serious threat.
In a standard web application, when a user sends a request, the server processes the request and may need to make additional requests to other resources, such as databases, APIs, or external services, to retrieve or process data. These server-side requests are usually made on behalf of the application and are considered trusted because they originate from the server itself. However, if the web application does not properly validate or sanitize user-supplied input that is used to create these server-side requests, an attacker can exploit this vulnerability to manipulate the requests and cause the server to send requests to random resources.
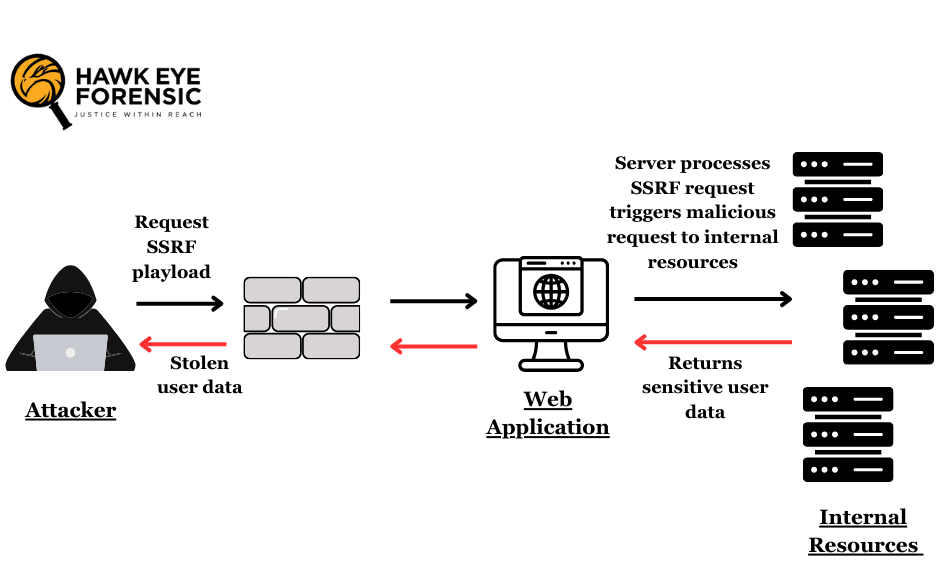
SSRF attacks can take various forms, depending on the specific vulnerabilities present and the attacker’s goals. Here are some common scenarios and techniques:
Addressing SSRF vulnerabilities requires a multi-faceted approach that combines secure coding practices, robust input validation, and proactive security testing. Here are some best practices for mitigating SSRF risks-
Server-Side Request Forgery (SSRF) is a critical web application vulnerability that can have far-reaching consequences if left unaddressed. By understanding the nature of SSRF attacks, their possible impact, and the various attack scenarios and techniques, organizations can take preventive steps to mitigate these risks and enhance the overall security posture of their web applications.
As the cyber threat landscape continues to evolve, staying alert and adopting a preventive approach to security is crucial. By prioritizing SSRF mitigation and fostering a culture of secure coding and secure application design, organizations can safeguard their web applications, protect sensitive data, and maintain the trust of their users and stakeholders.
Tagged as: Cloud Service Exploitation, Cyber Forensics, Server-Side Requests, URL Redirection, Cybercrimes, Internal Resources, File Upload Attacks, Digital Forensic, External Websites, Server-Side Request Smuggling, Cybercrime investigation, Input Validation, Blind SSRF, Penetration testing, Trusted Network Privileges, Template Injection, Server-Side Request Forgery, Data Exfiltration, Secure Libraries, SSRF Attack, Network Reconnaissance, Security Testing, SSRF, Port Scanning, Monitoring and Logging, Web Application Vulnerability, Service Abuse, Forensic Science, Cyber Attack, Metadata Disclosure, Malicious Input.

Virtual private networks (VPNs) have increased in popularity in recent years as more people look to protect their online privacy and security. A VPN encrypts your internet traffic and routes ...

Digital Forensics Anjali Singhal
Digital Forensics Anjali Singhal / May 20, 2024
Introduction In the modern digital landscape, the threat of malware looms large over individuals, businesses, and governments alike. Malware, short for malicious software, encompasses a variety of harmful programs designed to disrupt, damage, or gain unauthorized access to computer systems. With cyber threats becoming more sophisticated, the field of malware forensic analysis has become crucial. ...
Copyright 2023 all rights reserved by Hawk Eye Forensic.
Post comments (0)