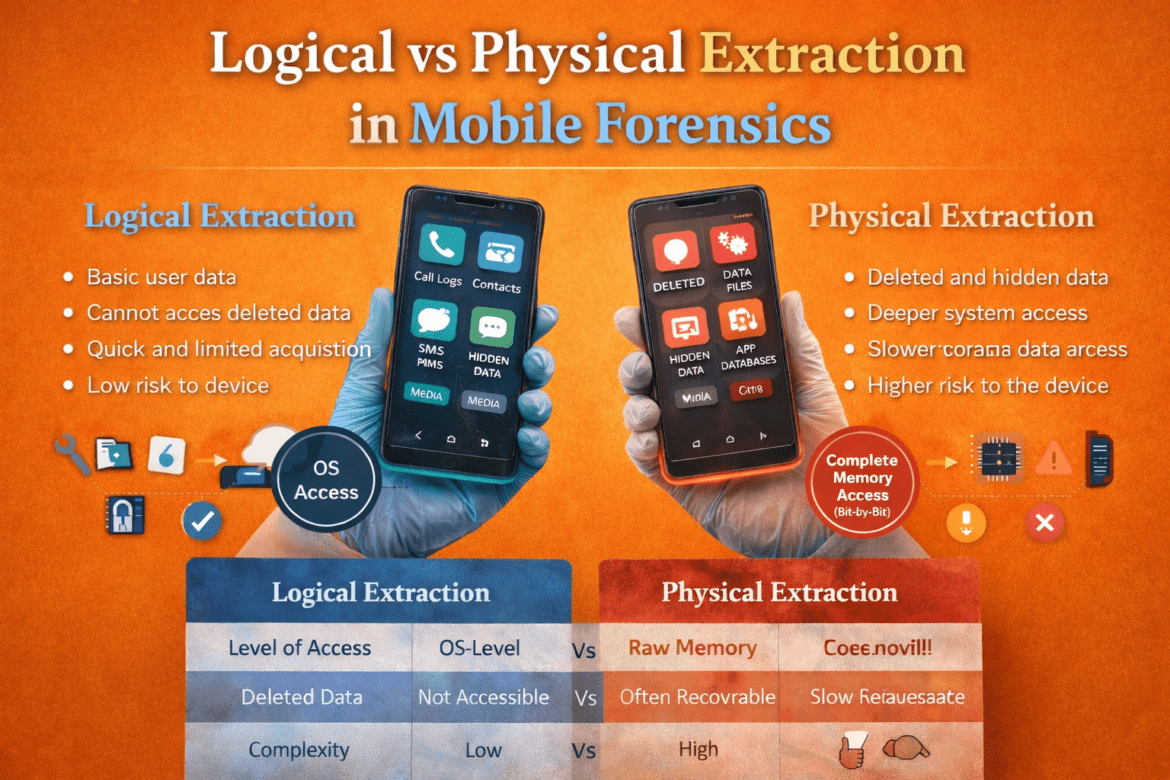
Logical vs Physical Extraction in Mobile Forensics
Logical vs Physical Extraction in Mobile Forensics Mobile phones have become one of the most critical sources of digital evidence in modern investigations. From communication records and location data to application activity and deleted content, smartphones store vast amounts of information. To access this data legally and scientifically, forensic experts ...