Introduction
Smartphones have become an integral part of daily life, storing vast amounts of personal, professional, and financial data. Consequently, they often play a critical role in criminal and civil investigations. However, with increasing concerns about privacy and data security, modern smartphones now use strong encryption mechanisms. While encryption protects users from unauthorized access, it also creates significant challenges for digital forensic investigators.
Encrypted smartphone investigations have become one of the most complex areas of digital forensics. Investigators must balance legal authority, technical limitations, and ethical considerations while attempting to extract relevant evidence. This blog explores the major challenges faced during encrypted smartphone investigations.
Understanding Smartphone Encryption
Smartphone encryption is a security process that converts data into an unreadable format, which can only be accessed using the correct credentials such as a PIN, password, pattern, or biometric authentication. Modern operating systems like Android and iOS use full-disk encryption (FDE) or file-based encryption (FBE).
As a result, even if investigators gain physical access to a device, the stored data often remains inaccessible without proper decryption keys. This strong security architecture significantly complicates forensic analysis.
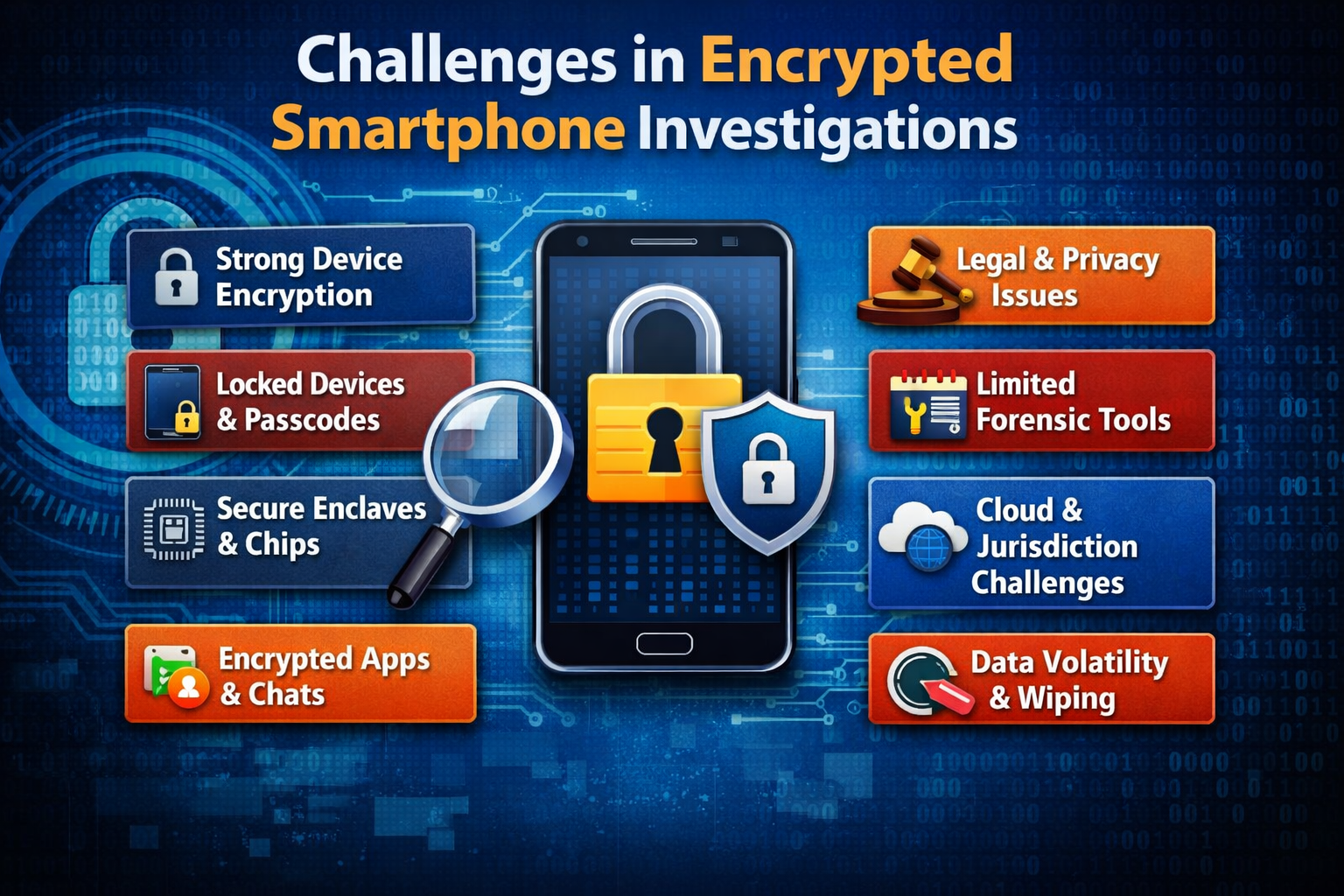
1. Strong Default Encryption
One of the primary challenges in smartphone investigations is that encryption is enabled by default on most modern devices. Unlike earlier mobile phones, current smartphones automatically encrypt user data as soon as the device is set up.
Therefore, traditional forensic techniques such as chip-off or manual extraction often fail to retrieve meaningful data. Even advanced forensic tools cannot bypass encryption without authentication credentials, making data access extremely difficult.
2. Lack of Passcode or Credentials
In many cases, investigators do not have access to the device passcode, password, or biometric information. Without these credentials, decrypting the smartphone becomes nearly impossible.
Moreover, repeated incorrect attempts may trigger security mechanisms such as:
-
Data wipe
-
Increased time delays
-
Permanent device lock
Consequently, brute-force attacks are rarely feasible, especially on newer devices with hardware-backed security.
3. Secure Enclaves and Hardware-Based Security
Modern smartphones use hardware-based security components, such as Apple’s Secure Enclave or Android’s Trusted Execution Environment (TEE). These components store encryption keys separately from the main operating system.
As a result, even if investigators extract raw data from the device storage, they cannot decrypt it without access to the secure hardware. This separation significantly limits the effectiveness of physical extraction methods.
4. Limited Forensic Tool Capabilities
Although digital forensic tools continue to evolve, they often struggle to keep pace with rapid advancements in smartphone security. Each new operating system update introduces enhanced encryption methods and security patches.
Therefore:
-
Tools may support only specific models or OS versions
-
Older exploits may stop working after updates
-
Zero-day vulnerabilities are rare and costly
As a result, investigators cannot rely solely on forensic software and must often explore alternative approaches.
5. Legal and Ethical Constraints
Encrypted smartphone investigations also face legal limitations. Even when investigators possess a valid warrant, compelling a suspect to disclose a passcode may not always be legally permissible, depending on jurisdiction.
Additionally:
-
Biometric access laws vary across countries
-
Privacy rights may restrict forced decryption
-
Evidence must be collected without violating constitutional protections
Thus, legal and ethical considerations often restrict the available investigative options.
6. Time Sensitivity and Data Volatility
Smartphone data is highly volatile. Encrypted devices may:
-
Automatically lock after inactivity
-
Re-encrypt data upon reboot
-
Erase data after multiple failed access attempts
Therefore, delays in forensic acquisition can permanently block access to critical evidence. Investigators must act quickly while ensuring they do not compromise the device.
7. Encrypted Applications and Messaging Platforms
Even if investigators successfully access a smartphone, many applications use end-to-end encryption, such as WhatsApp, Signal, and Telegram. These apps encrypt data at the application level, adding another layer of protection.
Consequently:
This dual-layer encryption significantly reduces the amount of recoverable evidence.
8. Cloud Dependency and Jurisdiction Issues
Modern smartphones heavily rely on cloud services for backups and synchronization. While cloud data may provide alternative evidence, accessing it introduces additional challenges.
For example:
-
Cloud data may also be encrypted
-
Service providers may require separate legal requests
-
Servers may be located in different countries
As a result, jurisdictional and legal complexities often delay or prevent evidence acquisition.
Conclusion
Encrypted smartphone investigations present one of the greatest challenges in modern digital forensics. Strong default encryption, hardware-based security, legal constraints, and rapid technological advancements collectively limit traditional forensic approaches. While encryption enhances user privacy and data protection, it simultaneously restricts investigators’ ability to access potential evidence.
To overcome these challenges, digital forensic professionals must continuously update their technical skills, understand legal boundaries, and adopt alternative investigative strategies such as cloud forensics, metadata analysis, and open-source intelligence. Ultimately, a balanced approach that respects privacy while enabling lawful investigation remains essential in the evolving digital landscape.



Post comments (0)