
Data recovery services in delhi
Data Recovery Services in Delhi – The Ultimate Data Recovery Solutions In today’s digital era, data is more valuable than ever. From personal memories to business-critical files, a single storage ...


Mobile Forensic Ayushi Agrawal todayJune 20, 2025

Hawk Eye Forensic are leaders in this sector, providing law enforcement and private clients with accurate, private, and court-admissible mobile forensic services.
The study of recovering digital evidence from mobile devices is known as mobile forensics. In contrast to traditional computer forensics, mobile forensics necessitates a thorough comprehension of hardware setups, application environments, and proprietary operating systems (Android, iOS, KaiOS, etc.).
At Hawk Eye Forensic, we treat each case with scientific rigor and legal sensitivity, ensuring that every piece of data is preserved, extracted, analyzed, and reported in a manner that withstands judicial scrutiny.
Our mobile forensic services include, but are not limited to:
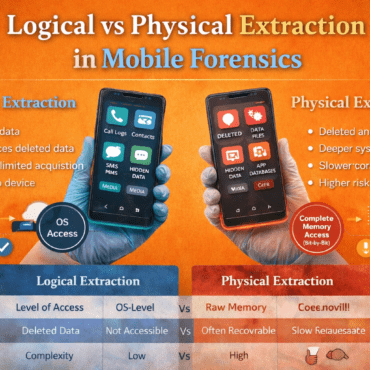
Modern phones offer robust security features including PINs, patterns, biometric locks, and full-disk encryption. Devices like iPhones with Secure Enclave or Android phones with File-Based Encryption (FBE) are extremely challenging to access without bypass tools.However, when legally authorized, our experts can extract critical data from locked or inaccessible devices using:
Criminal suspects unwilling to share passwords
Family disputes where one spouse’s phone needs to be forensically reviewed
The deceased person’s phone requiring access for investigation

One of the most in-demand services, deleted data recovery, involves retrieving information that has been removed from the user interface but still exists in residual system memory or app databases.
Forensic Approach:
Cellebrite Physical Analyzer: Extracts and decodes deleted data from SQLite databases.
Magnet AXIOM: Recovers timeline-based deleted records from messaging apps.
XRY Logical & Physical: Excellent for carving deleted content from chat apps.
Rooting & Jailbreaking (controlled environment): Allows full access to app data and protected partitions.
Using tools like Cellebrite Physical Analyzer, Magnet AXIOM, and MSAB XRY, we recover:
3. Damaged Phone Data Recovery
Physical damage doesn’t always mean data is unrecoverable. Our lab specializes in recovering data from:

Board-Level Repairs: Replacement of key components (PMIC, USB IC, Charging IC) to temporarily power the device.
Chip-Off Forensics: We remove the eMMC/UFS chip using BGA rework stations, read raw dumps with tools like UFI Box, Easy JTAG Plus.
JTAG Extraction: For MTK and Qualcomm phones, test points are soldered to extract NAND memory bit-by-bit.
Rebuild of Partition Tables: We reconstruct partitions using hex-level data and validate using known OS structures.
Most communication happens via apps, which use encrypted local databases and often don’t leave traces in device memory. Apps like WhatsApp, Signal, Telegram, and Snapchat are designed with user privacy in mind. We extract encrypted or deleted data from popular applications, including:

Decryption Keys: We extract key files from rooted Android or jailbroken iOS to decrypt SQLite DBs (msgstore.db for WhatsApp).
Token Extraction: From device RAM or settings, we extract session tokens to access Telegram or Instagram data.
Cloud APIs: We interface with WhatsApp’s Google Drive backup or iCloud for WhatsApp/iMessage/Signal recovery.
Cache & Media Analysis: Recover deleted media from app-specific folders (/Android/media/ or /WhatsApp/.shared)
Our tools can decrypt SQLite databases, decode base64 attachments, and interpret JSON logs
Even when a phone is lost or physically damaged beyond repair, users often back up their data to the cloud. With legal authorization, we retrieve data from:

For example, a client whose Realme phone was factory reset came to us for WhatsApp restoration. Using token-based Google authentication, we pulled the latest backup from their Google Drive account and restored the entire chat history.
We uncover evidence of unauthorized surveillance, such as:
Our forensic toolkit includes app permissions auditing, APK reverse engineering, and runtime behaviour analysis. In one marital dispute, spyware was found installed on a phone disguised as a file manager app, revealing months of illegal surveillance.
Sometimes, it’s not just what happened—but when and how—that matters. Our forensic analysis provides:
A suspicious death case was illuminated when we reconstructed 72 hours of activity from a Motorola phone, proving the user last accessed social media three hours after the alleged time of death.
Tools Used in Mobile Forensics
We employ state-of-the-art mobile forensic tools, ensuring coverage across all major mobile platforms:

We’ve successfully recovered data from:
Even phones with no power, no screen, or locked bootloaders have been successfully examined.
We support forensic analysis for a vast range of brands and models including:

At Hawk Eye Forensic, all analysis is done as per standard forensic protocol:




Written by: Ayushi Agrawal

Digital Forensics Omprakash Singh
Data Recovery Services in Delhi – The Ultimate Data Recovery Solutions In today’s digital era, data is more valuable than ever. From personal memories to business-critical files, a single storage ...

Copyright 2016-2025 all rights reserved by Hawk Eye Forensic.
Post comments (0)