
7 Powerful Algorithms for Permanently Erasing Files and Folders
Error deleting is never safe. In a file system, deleting a file just deletes the file’s entry (pointer) from the file index. Consequently, the actual data is still present on ...


Mobile Forensic Jay Ravtole todayMarch 26, 2024


Mobile devices provide a variety of possible acquisition opportunities. The capacity to collect a specific sort of acquisition will be determined by the mobile device’s make/model/operating system, as well as the lab’s accessible instruments. The mobile acquisitions include Full File System, Physical, Logical, After First Unlock (AFU), Before First Unlock (BFU), Manual, and System/Crash Logs.

Figure 1: Various Mobile Acquisitions
There are three key device conditions that will determine what acquisition sequence an examiner should take: Off, On and Unlocked, and On and Locked.

Figure 2: Three device conditions
Let us define some of the various acquisitions as they pertain to mobile, as these definitions differ from the typical acquisition kinds found in Mobile Forensics.

Figure 3: Workflow for a mobile device in the OFF condition

Figure 4: Initial steps for a mobile device in the ON and UNLOCKED condition

Figure 5: Continued workflow for a mobile device ON and UNLOCKED condition
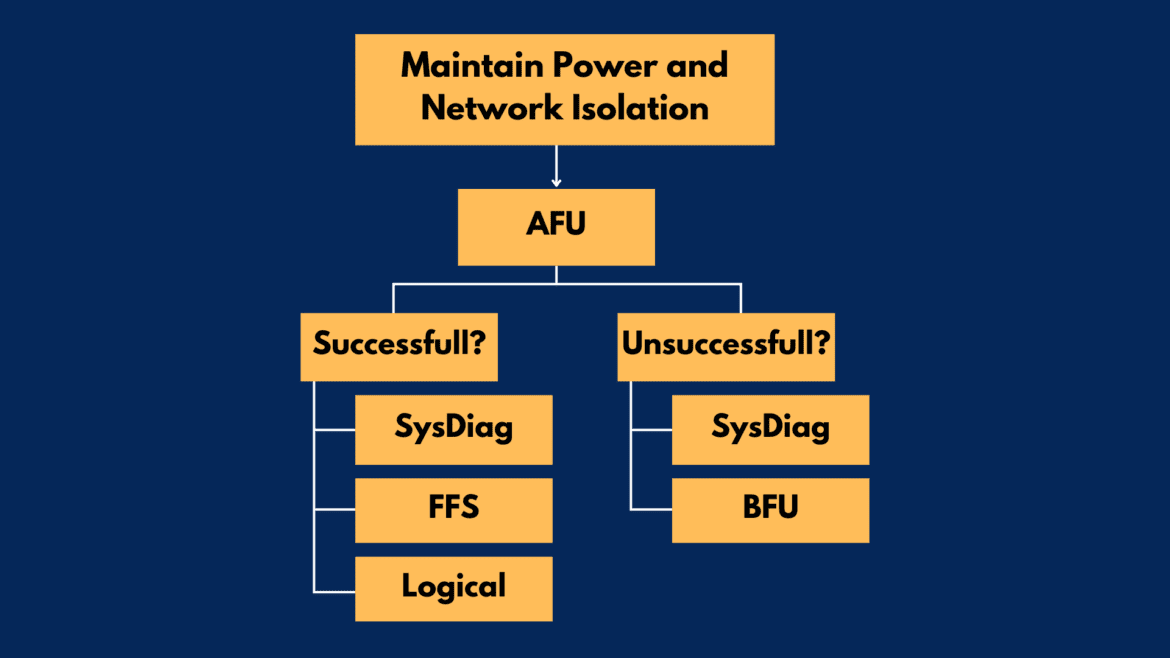
Figure 6: Workflow for mobile devices in ON and LOCKED condition
If you want to learn more about mobile forensic foundations and analysis, we recommend our HEF Certified Cyber Forensic Investigator (HEF-CCFi) training.
Written by: Jay Ravtole
Tagged as: mobile forensics, Smartphone recovery, hawk eye forensic lab, Mobile device restoration, data recovery, Data backup, Digital evidence, File recovery, Data Acquisition, Deleted data recovery, Investigative Procedures, Android/iOS recovery, Evidence preservation, Data recovery software, Forensic Examination, Mobile data backup, Data Retrieval, Data loss prevention, Hawk Eye Forensic, Digital investigation, Device prioritization.

Digital Forensics Jay Ravtole
Error deleting is never safe. In a file system, deleting a file just deletes the file’s entry (pointer) from the file index. Consequently, the actual data is still present on ...
Mobile Forensic Anjali Singhal / May 10, 2024
Introduction iOS devices have become an integral part of our daily lives, storing a vast array of personal and sensitive information. For forensic investigators and digital security professionals, accessing and analyzing data from iOS devices poses unique challenges due to Apple’s stringent security measures. In this blog post, we will delve into the common challenges ...

Copyright 2023 all rights reserved by Hawk Eye Forensic.
Post comments (0)