Introduction
In the ever-evolving landscape of forensic investigations, technological advancements have brought about a paradigm shift in how evidence is collected, analyzed, and presented in legal proceedings. One such crucial innovation is the advent of digital signatures, a cryptographic technique that plays a pivotal role in ensuring the integrity and authenticity of digital information. In forensic investigations, digital signatures have emerged as a powerful tool for validating the origin and integrity of electronic documents, communications, and transactions.
Understanding Digital Signatures
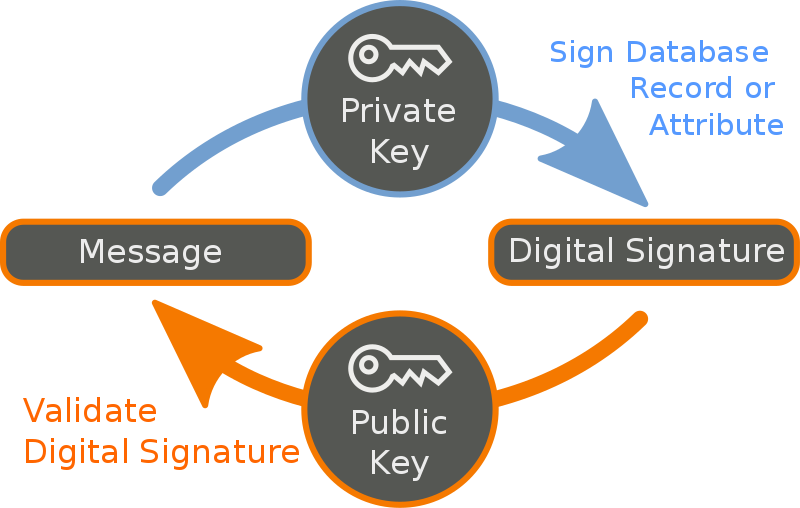
A digital signature is a mathematical algorithm that authenticates the identity of the sender, verifies the contents of a message or document, and ensures that the information has not been altered during transmission. Unlike traditional handwritten signatures, digital signatures rely on complex cryptographic techniques involving public and private key pairs.
When a user digitally signs a document, their private key generates a unique digital fingerprint known as a hash. This hash is then encrypted using the private key provided by the sender to produce the digital signature. Recipients can use the sender’s public key to decrypt the signature and verify its authenticity by comparing the decrypted hash with a newly generated hash of the received document. Any alterations to the document would result in a mismatch, indicating tampering or unauthorized changes.
Digital signatures are cryptographic tools used to verify the authenticity, integrity, and non-repudiation of digital data or documents. They serve as the digital equivalent of handwritten signatures in the physical world, but with added security measures and capabilities due to their cryptographic nature.
Components of Digital Signatures
Digital signatures are used to ensure the authenticity, integrity, and non-repudiation of digital documents and transactions. The key elements of a digital signature include:
- Hash function: A hash function is used to generate a unique message digest or fingerprint of the data to be signed. This ensures that any modification of the data can be easily detected.
- Private key: A private key is used to generate the digital signature. It is kept secret by the signer and should not be shared with anyone else.
- Public key: A public key is used to verify the digital signature. It can be freely distributed and is used by the recipient to verify the authenticity of the signed data.
- Signature algorithm: A signature algorithm is used to combine the private key with the message digest to create the digital signature.
- Certificate: A certificate is a digital document that contains information about the signer, the public key, and the certificate authority that issued the certificate. It is used to verify the authenticity of the public key.
- Timestamp: A timestamp is used to record the time when the digital signature was created. This is important for legal purposes and to prevent replay attacks.
Types of digital signatures
Digital signatures can be categorized based on their underlying technology, the purpose they serve, or the methods used for implementation. Here are some types of digital signatures:
- Basic Electronic Signatures:
Basic electronic signatures are the simplest form and often involve methods like scanned images of handwritten signatures, typed names, or clicking “I agree” checkboxes in electronic documents. They lack the cryptographic security of more advanced digital signatures.
- Advanced Electronic Signatures (AES):
Advanced electronic signatures use cryptographic techniques to ensure integrity and authenticity. They include digital signatures created with digital certificates issued by trusted Certificate Authorities (CAs). AES provides higher security and is legally recognized in many jurisdictions.
- Qualified Electronic Signatures (QES):
Qualified electronic signatures, also known as digital signatures in some regions, meet specific legal requirements set by regulations such as the European Union’s eIDAS (Electronic Identification and Trust Services) Regulation. QES employs a qualified digital certificate from an accredited provider and carries a higher level of legal validity.
- Cryptographic Digital Signatures:
Cryptographic digital signatures are based on cryptographic algorithms that use key pairs (private and public keys) to create and verify signatures. These signatures ensure data integrity and non-repudiation. Common cryptographic algorithms include RSA, DSA (Digital Signature Algorithm), and ECDSA (Elliptic Curve Digital Signature Algorithm).
- Biometric Digital Signatures:
Biometric digital signatures involve using biometric data, such as fingerprints or retina scans, to create a unique identifier for signing documents. These signatures offer high security by tying the signature directly to the individual’s biological characteristics.
- One-Time Digital Signatures:
One-time digital signatures are used for a single specific transaction or document. They are generated using cryptographic techniques and can be used only once, ensuring the uniqueness of the signature for each instance.
Multiple signatures involve the signing of a document by multiple parties. Each signer’s digital signature is added to the document, allowing verification of each individual’s approval or authorization.
Role/Applications of Digital Signatures in Forensic Investigations
The applications of digital signatures in forensic investigations is significant due to their pivotal role in validating, preserving, and ensuring the integrity of digital evidence.
- Data Integrity Verification:
Digital signatures play a vital role in verifying the integrity of digital data. In forensic investigations, they help ensure that digital evidence, such as files, emails, or documents, has not been tampered with or altered. By comparing the original signed data with its current state, investigators can verify if any changes have occurred.
- Establishing Authenticity:
One primary application of digital signatures in forensics is verifying the authenticity of digital documents or communications. They confirm the origin of the data and assure the sender’s identity, enabling investigators to establish the credibility of evidence.
- Chain of Custody Maintenance:
Maintaining a clear and secure chain of custody is essential in forensic investigations. Digital signatures create a time-stamped record of when and by whom digital evidence was accessed, modified, or transferred. This helps establish the integrity and continuity of evidence, enhancing its admissibility in court.
Digital signatures ensure non-repudiation, preventing signatories from denying their involvement or disowning the content of digitally signed documents. This aspect holds significance in legal proceedings, as it establishes accountability and prevents individuals from denying their actions.
- Fraud Detection and Investigation:
In cases involving financial fraud, cybercrimes, or data breaches, digital signatures aid investigators in identifying unauthorized alterations or fraudulent activities. They enable experts to trace the history of digital documents, pinpointing when changes occurred and identifying potential fraudulent behaviour.
- Legal Admissibility and Compliance:
Digital signatures, when implemented following relevant standards and guidelines, hold legal weight similar to traditional handwritten signatures. They provide verifiable evidence that can be presented in court, supporting the authenticity and integrity of digital evidence in legal proceedings.
- Secure Document Authentication:
Digital signatures facilitate secure authentication of sensitive documents, ensuring that they have not been manipulated or altered. This is particularly critical in industries like healthcare, finance, and government, where document authenticity and integrity are paramount.
By employing digital signatures, forensic investigators can preserve the original state of digital evidence. This helps in maintaining the evidentiary value of data by ensuring its integrity and authenticity throughout the investigation process.
Challenges
- Key Management and Security Risks
The management of cryptographic keys poses a significant challenge in the utilization of digital signatures. Safeguarding private keys from unauthorized access or theft is crucial. Breaches in key management can compromise the integrity of digital signatures, leading to potential forgeries or tampering.
- Certificate Authority Reliability
Digital signatures rely on trusted certificate authorities (CAs) to validate public keys. However, issues like compromised CAs or expired certificates can undermine the trustworthiness of digital signatures. Constant monitoring and authentication of CAs are essential to mitigate such risks.
- Interoperability and Standards
Ensuring interoperability among various digital signature solutions and adherence to established standards is another challenge. Different platforms, file formats, or encryption protocols may hinder seamless verification and validation of digital signatures across systems.
- Evolving Cryptographic Vulnerabilities
Advancements in computing power pose a threat to existing cryptographic algorithms. The emergence of quantum computing, for instance, could render current encryption methods obsolete, necessitating the development of quantum-resistant cryptographic solutions.
Future Developments
The future of digital signatures in forensic investigations is poised for advancements that aim to enhance security, efficiency, and adaptability to evolving technological landscapes. Anticipated future developments include:
- Quantum-Resistant Cryptography:
As the threat of quantum computing grows, the development and adoption of quantum-resistant cryptographic methods will be crucial. Future digital signatures are likely to incorporate algorithms resistant to quantum attacks, ensuring the continued security of signed data against emerging threats.
Further integration of digital signatures with blockchain technology is expected. Blockchain’s immutable nature and decentralized verification can fortify the security and transparency of digital signatures. This integration will enhance the reliability and traceability of signatures in forensic investigations.
- Enhanced Authentication Mechanisms:
Future digital signatures may involve advanced authentication methods such as biometrics, multi-factor authentication, or secure hardware tokens. These additional layers of security can bolster the protection of private keys, strengthening the overall integrity of digital signatures.
- Standardization and Regulatory Frameworks:
Efforts toward global standardization and regulatory frameworks specific to digital signatures in forensic investigations are crucial. Clear guidelines and compliance measures will streamline the use of digital signatures, ensuring consistency, reliability, and legal admissibility across different jurisdictions.
- Continued Evolution of Anti-Forensic Techniques:
As digital signatures advance, so do anti-forensic techniques aimed at undermining their integrity. Forensic investigators must evolve their methodologies to counter new and sophisticated attempts to tamper with or circumvent digital signatures.
- Machine Learning and Artificial Intelligence:
The integration of machine learning and AI algorithms can aid in detecting anomalies, identifying patterns, and automating certain aspects of digital signature verification. These technologies may enhance the efficiency and accuracy of forensic investigations involving digital signatures.
- Privacy-Preserving Techniques:
Future developments will likely focus on striking a balance between investigative access to digital evidence and preserving individual privacy rights. Innovations in privacy-preserving techniques will aim to protect sensitive information while enabling effective forensic analysis.
Conclusion
Digital signatures have revolutionized forensic investigations by providing a means to authenticate, validate, and preserve the integrity of digital information. Their role in ensuring data integrity, establishing authenticity, and supporting the chain of custody makes them indispensable tools for forensic experts and legal professionals alike. However, to harness their full potential, addressing challenges such as key management, standardization, and emerging threats is imperative.
Future developments are poised to shape the evolution of digital signatures within forensic landscapes. Emphasis on quantum-resistant cryptography, block chain integration, enhanced authentication mechanisms, and regulatory frameworks will fortify the role of digital signatures in ensuring the authenticity and integrity of digital evidence. Staying ahead of these advancements will be key in safeguarding the credibility and reliability of digital evidence in forensic investigations.
References:
- Chandrashekhara, J., V B, A., H, P. and B R, R. (2021). A COMPREHENSIVE STUDY ON DIGITAL SIGNATURE. International Journal of Innovative Research in Computer Science & Technology, 9(3). doi:https://doi.org/10.21276/ijircst.2021.9.3.7.
- ResearchGate. (n.d.). (PDF) Digital Forensics: Review of Issues in Scientific Validation of Digital Evidence. [online] Available at: https://www.researchgate.net/publication/327644306_Digital_Forensics_Review_of_Issues_in_Scientific_Validation_of_Digital_Evidence.





Post comments (0)