
Cyber Forensic Laboratory
Cyber Forensic Laboratory Purpose and Vision of Hawk Eye Forensic Hawk Eye Forensic is a pioneering force in the digital forensic landscape, delivering end-to-end cyber forensic services to law enforcement, ...


Blog Ayushi Agrawal todayJuly 18, 2025

In an increasingly digital world, hard drives have become the backbone of data storage — for individuals, businesses, and even law enforcement. But when these hard drives fail — whether due to mechanical issues, physical damage, or logical corruption — critical data can seem permanently lost. Fortunately, forensic data recovery experts can often retrieve data even from severely damaged or “dead” hard drives using advanced techniques and specialised tools.
In this blog, we will walk you through how forensic professionals recover data from damaged or dead hard drives, the tools they use, common scenarios they face, and why such recovery is crucial in both personal and legal investigations.
Understanding the nature of the failure helps determine the best recovery strategy:
When the hard disk is accessible but data cannot be read due to file system corruption, partition loss, or accidental deletion.
Involves damage to internal components such as platters, heads, or motors. Causes include drops, overheating, or water/fire exposure.
PCB or controller board damage renders the disk unreadable or unresponsive.
When internal microcode controlling the drive becomes corrupted, the disk fails to initialize or becomes stuck in busy mode.
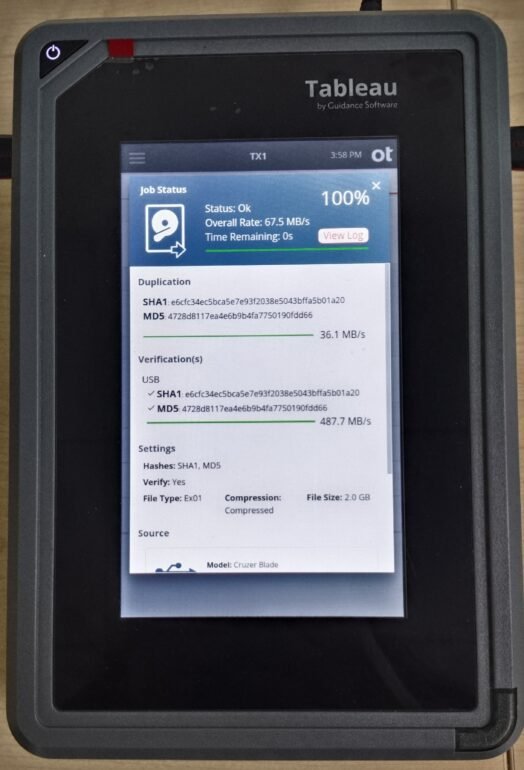
Our process starts with safe assessment using Tableau Forensic Hardware, including:
Tableau TX1 Forensic Imager for write-blocked previews
Tableau Forensic Bridges and Duplicators to safely access drives without altering evidence
These tools allow us to determine whether the drive can be imaged, cloned, or requires deeper intervention.

If the drive is responsive, we create a bit-for-bit forensic image using:
TX1 Forensic Imager – One of the most advanced duplicators, supporting SATA, IDE, SAS, USB, NVMe, and more, ensuring fast and validated acquisition.
Falcon-NEO Imager – Used for high-speed imaging with advanced hashing, encryption, and destination duplication.
These tools offer write-blocked acquisition, ensuring evidentiary integrity and compliance with legal standards under Section 63(4)(c) of the Bharatiya Sakshya Adhiniyam (BSA).
Once the forensic image is created, our analysts use EnCase Forensic Software, a globally recognised standard in digital forensics, to:
Recover deleted files and hidden partitions
Identify timestamped user activity
Extract and reconstruct fragmented files
Analyze system logs, browser histories, chats, and other metadata
EnCase also enables timeline analysis, email parsing, registry analysis, and keyword-based searches—critical in cybercrime and legal investigations.
Recovered data is extracted from the image and documented in a legally sound manner. Our final deliverables include:
Detailed Forensic Report
Hash value validation (MD5/SHA-1/SHA-256)
Certificate under Section 63(4)(c) of the Bharatiya Sakshya Adhiniyam (BSA)
List of Recovered Files & Metadata
All procedures followed at Hawk Eye Forensic ensure the chain of custody is maintained from receipt to reporting, enabling the report to be admissible in court.
Forensic investigations on damaged hard drives come with unique challenges:
Drives damaged by fire, water, or impact require specialized lab environments.
Cleanroom facilities are often needed to disassemble and repair drives.
Modern hard drives often use encryption, making data recovery complex.
Decryption keys or brute-force techniques may be required.
High-capacity drives store enormous amounts of data, increasing recovery time.
We are an accredited forensic lab trusted by law enforcement, corporations, legal firms, and the judiciary.
We invest in top-tier forensic hardware:
TX1 Forensic Imager
Falcon-NEO
Tableau Write-Blockers
We issue digitally signed forensic reports, certified under 63(4)(c), admissible in all Indian courts.
We work on forensic clones only, keeping your original evidence untouched. Confidentiality and data privacy are strictly maintained.
Conclusion
Recovering data from a dead or damaged hard drive isn’t just about retrieving files—it’s about uncovering the truth, restoring evidence, and preserving digital history. At Hawk Eye Forensic, we use globally certified tools like TX1, Falcon-NEO, Tableau, and EnCase to ensure every bit of data is retrieved scientifically and securely.
Whether you’re dealing with personal data loss or handling a high-profile cybercrime case, our team of forensic experts is ready to assist.
Written by: Ayushi Agrawal

Cyber Forensic Omprakash Singh
Cyber Forensic Laboratory Purpose and Vision of Hawk Eye Forensic Hawk Eye Forensic is a pioneering force in the digital forensic landscape, delivering end-to-end cyber forensic services to law enforcement, ...

Copyright 2016-2025 all rights reserved by Hawk Eye Forensic.
Post comments (0)