Windows Forensics: Introduction to Windows Registry Forensics
In the world of digital forensics, every digital footprint counts — and when it comes to Windows systems, the Windows Registry is one of the richest sources of evidence. It contains traces of user activity, system configurations, connected devices, and software executions — all essential for forensic investigators.
This blog introduces Windows Registry Forensics, covering how experts acquire, analyze, and interpret critical data to uncover digital evidence in criminal or cybersecurity investigations.
What Is Windows Registry Forensics?
The Windows Registry is a centralized hierarchical database that stores configuration settings and user preferences for the operating system, applications, and hardware.
In forensics, Windows Registry Forensics involves analyzing this data to identify patterns of user behavior, installed applications, connected devices, and evidence of execution.
Registry forensics helps investigators reconstruct timelines, verify user activity, and trace malicious behavior in Windows environments.
Understanding the Windows Registry
The Registry is divided into several key sections called hives, each storing different types of information. Common registry hives include:
-
SAM (Security Account Manager): Stores user account information and security identifiers (SIDs).
-
SYSTEM: Contains system configuration data such as hardware settings and boot information.
-
SOFTWARE: Includes installed software details and application settings.
-
SECURITY: Holds local security policy configurations.
-
NTUSER.DAT and UsrClass.dat: Store user-specific data like desktop preferences, network connections, and recently accessed files.
These hives are crucial for investigators because they can reveal who used the system, when, and how.
Accessing Registry Hives Offline
One of the key forensic techniques is accessing registry hives offline — analyzing them from a forensic image or a copied disk without altering the original evidence.
Investigators use tools like FTK Imager, Registry Viewer, or Autopsy to safely mount and examine registry files. Offline access ensures data integrity and maintains the chain of custody, a critical factor in digital investigations.
Common registry hive file locations (in Windows 10/11):
C:\Windows\System32\config\
C:\Users\<username>\NTUSER.DAT
C:\Users\<username>\AppData\Local\Microsoft\Windows\UsrClass.dat
Data Acquisition in Windows Registry Forensics
Data acquisition is the process of securely collecting registry data for analysis. Investigators create a forensic image or extract specific registry hives using write-blocking tools to prevent accidental modification.
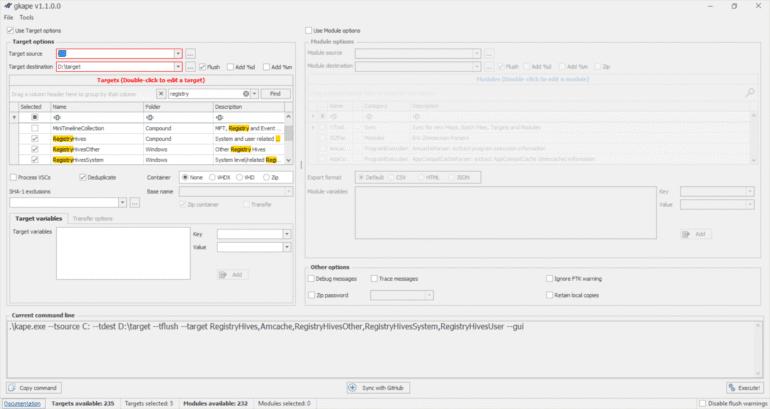
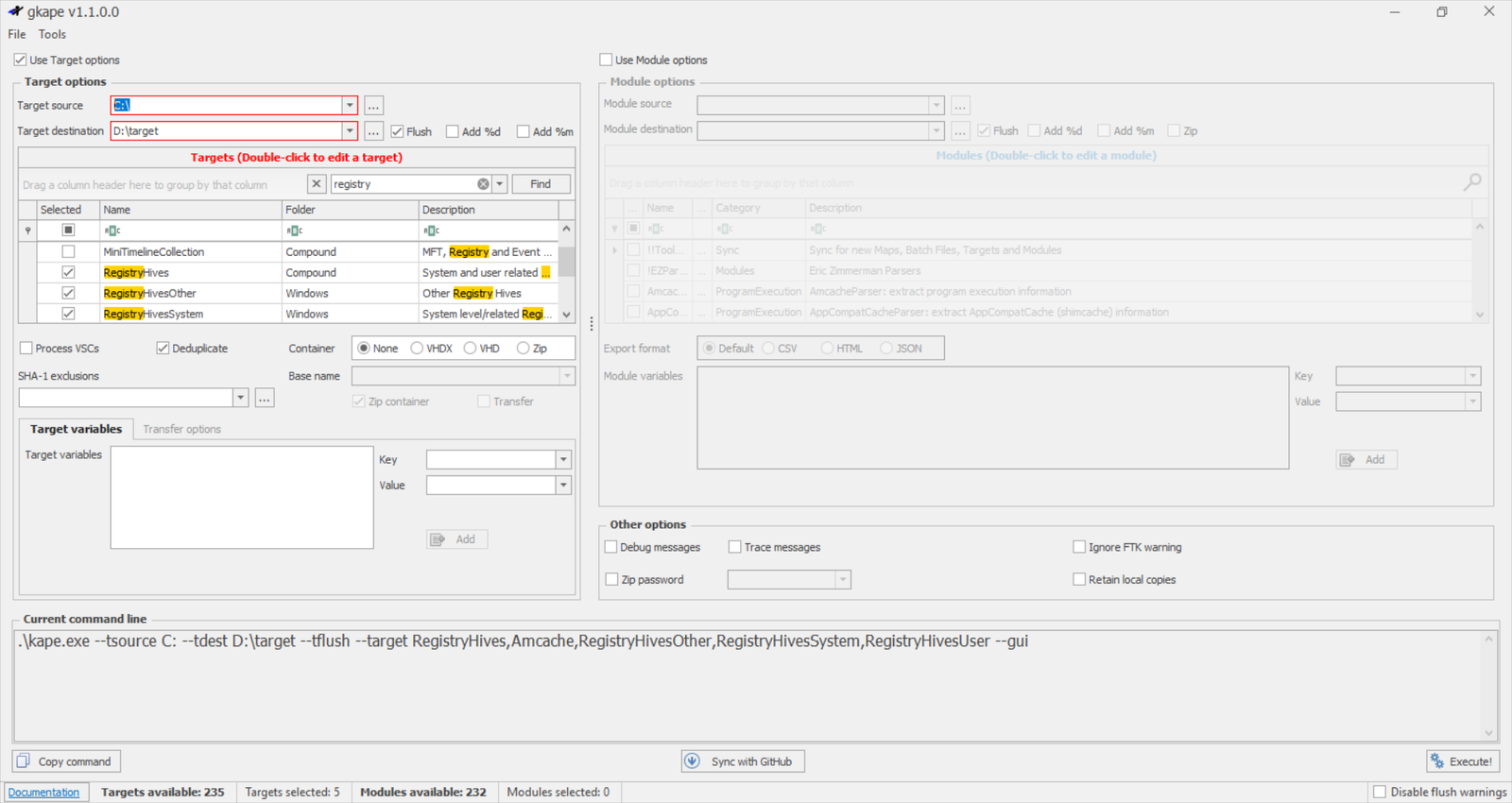
KAPE:
KAPE is a live data acquisition and analysis tool which can be used to acquire registry data. It is primarily a command-line tool but also comes with a GUI. The below screenshot shows what the KAPE GUI looks like. We have already selected all the settings to extract the registry data using KAPE in this screenshot. We will learn more about collecting forensic artifacts using KAPE in a dedicated KAPE room.
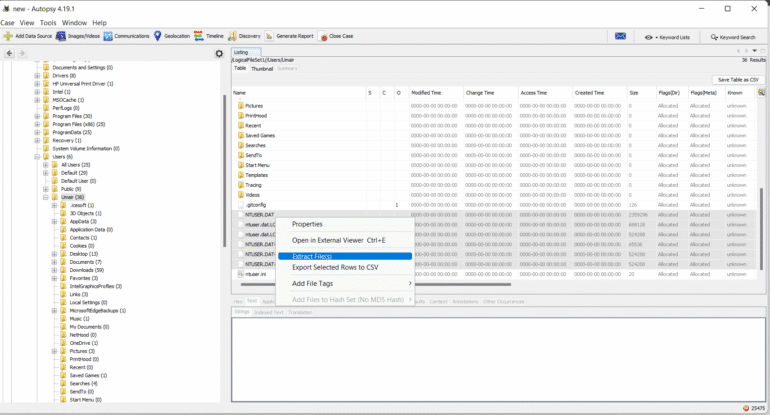
Autopsy:
Autopsy gives you the option to acquire data from both live systems or from a disk image. After adding your data source, navigate to the location of the files you want to extract, then right-click and select the Extract File(s) option. It will look similar to what you see in the screenshot below.

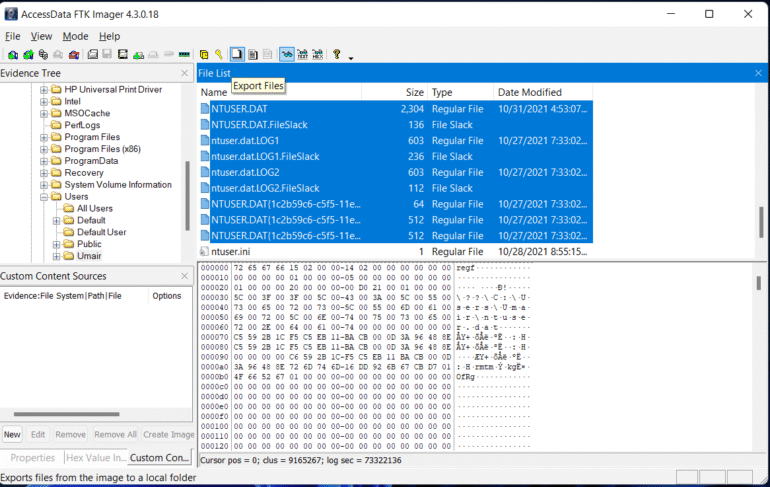
FTK Imager:
FTK Imager is similar to Autopsy and allows you to extract files from a disk image or a live system by mounting the said disk image or drive in FTK Imager. Below you can see the option to Export files as highlighted in the screenshot.

Methods of acquisition include:
Tools like EnCase, Magnet AXIOM, and Belkasoft are commonly used for forensic data acquisition and registry parsing.
Exploring the Windows Registry
Once data is acquired, forensic experts explore registry entries to locate evidence of user and system activity. Areas of interest include:
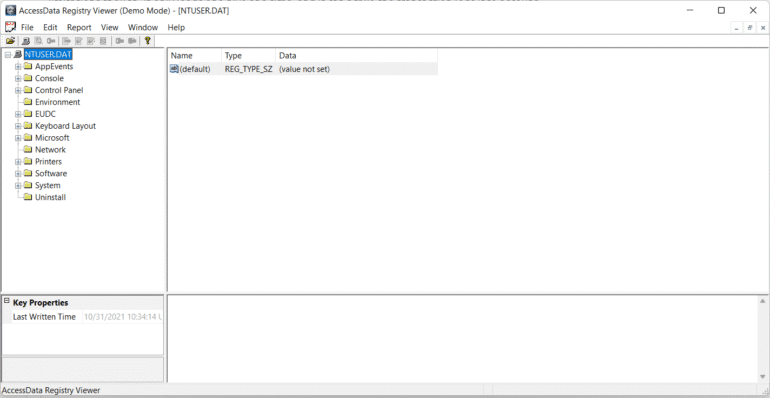
Registry Viewer:
As we can see in the screenshot below, AccessData’s Registry Viewer has a similar user interface to the Windows Registry Editor. There are a couple of limitations, though. It only loads one hive at a time, and it can’t take the transaction logs into account.

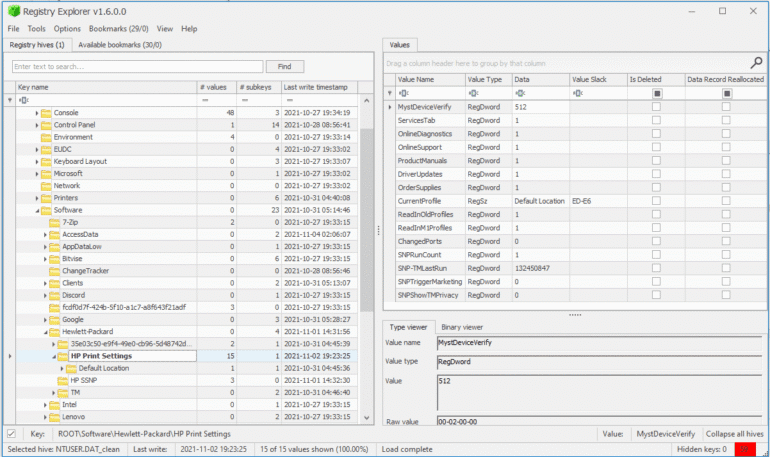
Zimmerman’s Registry Explorer:
Eric Zimmerman has developed a handful of tools that are very useful for performing Digital Forensics and Incident Response. One of them is the Registry Explorer. It looks like the below screenshot

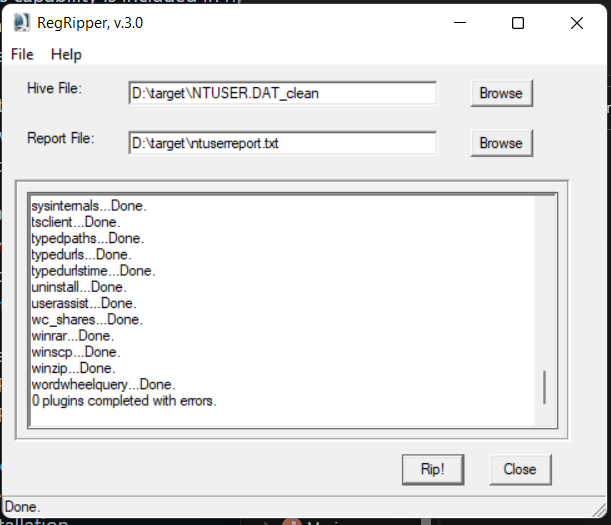
RegRipper:
RegRipper is a utility that takes a registry hive as input and outputs a report that extracts data from some of the forensically important keys and values in that hive. The output report is in a text file and shows all the results in sequential order.
RegRipper is available in both a CLI and GUI form which is shown in the screenshot below.

-
Recent Files/Applications: Tracks what was opened and when.
-
Run Keys: Show which programs run automatically at startup.
-
UserAssist: Reveals applications recently launched by a user.
-
ShellBags: Provide information about folders accessed in Windows Explorer.
-
Network Information: Logs of connected Wi-Fi networks and mapped drives.
Each of these artifacts can be pivotal in reconstructing a suspect’s activity timeline.
System Information and System Accounts
The SYSTEM and SAM hives contain data about hardware, system boot configuration, and local user accounts.
-
SYSTEM hive: Includes computer name, timezone, and USB device history.
-
SAM hive: Stores encrypted passwords and login attempts.
-
SECURITY hive: Holds policies defining user permissions and access control.
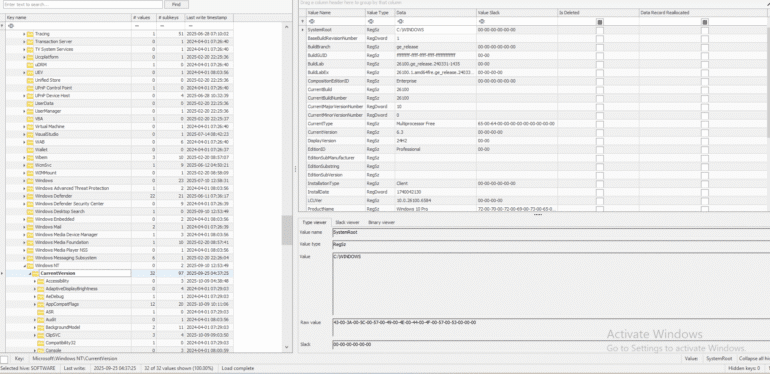
OS Version:
If we only have triage data to perform forensics, we can determine the OS version from which this data was pulled through the registry. To find the OS version, we can use the following registry key:
SOFTWARE\Microsoft\Windows NT\CurrentVersion

Computer Name:
It is crucial to establish the Computer Name while performing forensic analysis to ensure that we are working on the machine we are supposed to work on. We can find the Computer Name from the following location:
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
By analyzing these, investigators can determine who used the system, when it was last accessed, and whether unauthorized logins occurred.
Usage or Knowledge of Files and Folders
The registry provides valuable evidence about user interaction with files and folders. Investigators often examine:
-
MRU (Most Recently Used) Lists: Track recently accessed files.
-
OpenSaveMRU: Records documents opened or saved through standard dialogs.
-
RecentDocs: Contains a list of recently accessed documents by file extension.
These records help verify whether a suspect knew about specific files or intentionally accessed or deleted them.
Evidence of Execution
Evidence of execution helps investigators confirm which programs were executed on a system.
Key registry locations include:
-
RunMRU and UserAssist: Show recently executed applications.
-
AppCompatCache (ShimCache): Tracks programs previously run on the system.
-
Prefetch Files: Provide timestamps and frequency of application launches.
Together, these artifacts help build a timeline of user activity and detect potential malicious behavior.
External Devices / USB Device Forensics
Windows keeps detailed logs of all USB storage devices ever connected to the system.
Registry locations like:
SYSTEM\CurrentControlSet\Enum\USBSTOR
SYSTEM\MountedDevices
contain information such as device name, serial number, and connection timestamps.
This allows investigators to determine which external devices were used, when they were connected, and whether data was transferred — crucial in data theft or insider threat cases.
Conclusion
The Windows Registry is a goldmine of digital evidence. From user behavior and software usage to external device history, it reveals nearly every interaction on a Windows system.
Windows Registry Forensics empowers investigators to reconstruct timelines, validate user activity, and uncover critical evidence that traditional searches may miss.
As cybercrimes become more sophisticated, mastering registry forensics is essential for every digital forensic examiner, incident responder, and law enforcement investigator to ensure truth and justice in the digital age.




Post comments (0)