Smartphones have taken center stage in our lives in the digital age, holding anything from financial information and private conversations to multimedia, documents, and even location history. Due to their vast amount of data, mobile phones are an essential piece of evidence in contemporary investigations. However, what occurs if the data is erased? Is it still recoverable?
Here comes mobile forensics, a subfield of digital forensics that focuses on recovering and examining data from mobile devices, even after it has been erased. This blog explores the methods used by forensic specialists to recover erased data, the equipment they employ (including well-known companies like Cellebrite), and real-world examples where this recovery was essential to an investigation.
What Is Mobile Forensics?
Mobile forensics involves the recovery, analysis, and preservation of digital evidence from mobile devices, such as smartphones, tablets, and GPS units. The process must be conducted in a manner that maintains the integrity and admissibility of evidence in a court of law.
This discipline has grown exponentially with the evolution of mobile technology. With billions of smartphones in use worldwide, these devices have become goldmines of digital evidence in criminal, civil, and corporate investigations.

Techniques for Recovering Deleted Data
Recovering deleted data from a smartphone is a complex and meticulous task. It requires a deep understanding of mobile operating systems, file systems, storage structures, and encryption. Here are the most commonly used forensic acquisition techniques, explained in detail:

1. Logical Acquisition
What it is:
Logical acquisition extracts files and directories that are accessible through the device’s operating system (OS). It uses APIs provided by the OS to pull data like contacts, messages, call logs, and media.
Tools Used: Cellebrite UFED, Oxygen Forensics, MOBILedit.
Data Types Recovered:
Limitations:
-
Cannot recover deleted data.
-
Cannot access unallocated space or hidden system files.
-
Limited by OS restrictions (especially in iOS).
2. File System Acquisition
What it is:
This technique goes deeper than logical acquisition. It accesses the file system of the device, retrieving active files as well as artifacts of deleted data (such as remnants in SQLite databases, logs, or temporary folders).
Tools Used: Magnet AXIOM, Cellebrite UFED, MSAB XRY.
Data Types Recovered:
Why it’s useful:
Many mobile apps, including WhatsApp and Facebook, use local databases (e.g., SQLite). These may retain records even after deletion. Forensic tools can analyze freed pages in SQLite to carve out deleted messages.
Limitations:
3. Physical Acquisition
What it is:
This involves creating a bit-by-bit copy of the entire flash memory of the phone, including unallocated space, deleted files, and hidden partitions. Think of it as cloning the entire storage—raw data and all.
Tools Used: Cellebrite UFED, XRY, Oxygen Forensics.
Data Types Recovered:
-
Deleted messages and call logs
-
Deleted photos and videos
-
System artifacts and logs
-
Full app data (even protected content)
-
Hidden files, encrypted files, and configuration files
Advantages:
-
Most comprehensive form of data acquisition.
-
High success rate in recovering deleted content.
-
Access to deep system logs and memory artifacts.
Limitations:
-
Not supported on all devices due to secure bootloaders and encryption.
-
Some newer devices have hardware-based encryption (e.g., Secure Enclave in iPhones) which complicates physical acquisition.
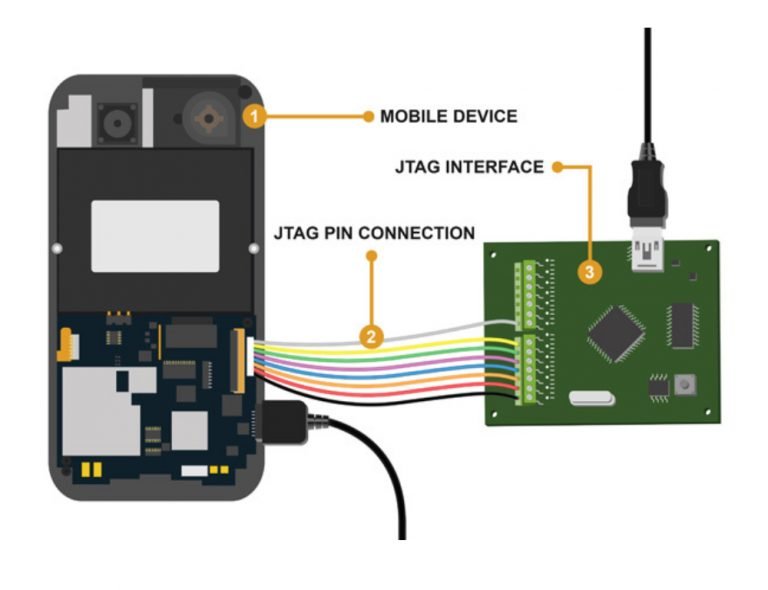
4. JTAG Extraction (Joint Test Action Group)

What it is:
JTAG is a hardware-based acquisition technique where forensic experts connect directly to the device’s motherboard using test points. It enables access to the raw memory chip without interacting with the operating system.
How it works:
-
Technicians disassemble the phone.
-
Connect probes to specific test points on the board.
-
Use a JTAG controller to read the NAND/NOR memory.
-
Dump the memory for analysis using forensic tools.
Data Types Recovered:
-
Deleted content (photos, texts, etc.)
-
Device configurations
-
Hidden partitions
-
Data from locked or bricked phones
Ideal for:
-
Devices with broken screens
-
Phones with non-functioning OS
-
Situations where traditional access is impossible
Challenges:
5. Chip-Off Forensics

What it is:
Chip-off is an extreme-level technique where the memory chip is physically desoldered from the mobile device and read using a dedicated chip reader.
Steps:
-
Carefully remove NAND flash memory chip from motherboard.
-
Clean and prepare the chip.
-
Insert into specialized chip reader (e.g., eMMC adapter).
-
Extract raw memory image.
-
Analyze using software like Cellebrite or Magnet AXIOM.
Data Types Recovered:
Use Cases:
-
Phones that are physically damaged, waterlogged, or burnt
-
Phones with hardware-enforced bootloaders
Challenges:
-
Irreversible; phone cannot be used again.
-
Risk of destroying chip if not handled properly.
-
Legally sensitive—must be justified and well-documented.
6. Cloud Data Acquisition

What it is:
Many users sync their phone data with cloud services like iCloud, Google Drive, OneDrive, or proprietary app clouds (like WhatsApp Cloud Backup). Investigators can access synced or backed-up data using legal warrants or tokens from the phone.
Tools Used: Elcomsoft Cloud Explorer, Magnet AXIOM Cloud, Oxygen Forensics Cloud Extractor.
Data Types Recovered:
-
iCloud/Google backups
-
WhatsApp backups
-
Email
-
Notes, calendars, app data
-
GPS history, activity logs
Benefits:
-
No need to unlock the physical phone.
-
Access to historical data across multiple devices.
-
Can recover data deleted from the device but still present in the cloud.
Limitations:
-
Requires legal access or credentials.
-
Two-factor authentication can be a barrier.
-
Data in the cloud may be encrypted with a separate key.
7. RAM Dump and Live Acquisition
What it is:
In rare cases, live acquisition techniques are used to extract volatile data from RAM before the device is shut down. This method is valuable for gathering information about open apps, running processes, or encryption keys that are not stored on disk.
Tools: Volatility Framework, custom scripts, and memory dumping tools (mostly used in Android root mode).
Data Types Recovered:
Limitations:
-
Must be performed on a live, unlocked device.
-
Volatile memory is erased once the phone powers off.
-
Technically challenging and not common in mobile forensics.
Key Tools in Mobile Forensics
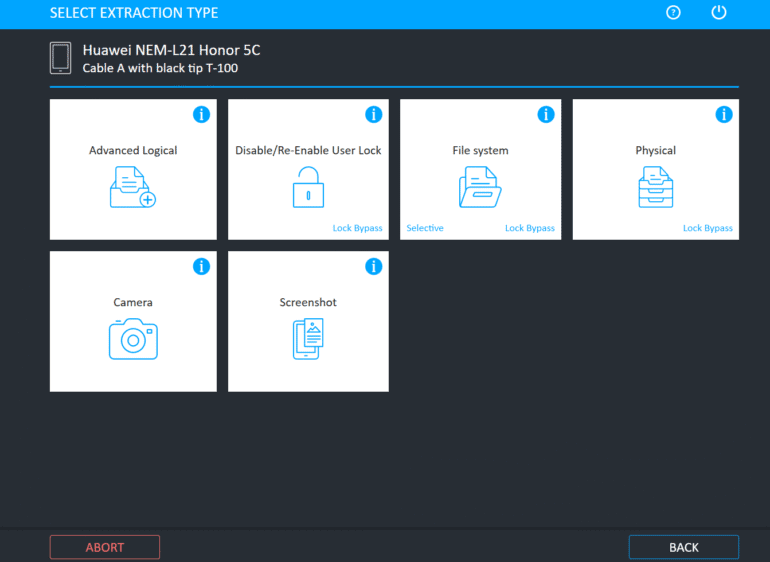
1. Cellebrite UFED (Universal Forensic Extraction Device)

Cellebrite is a global leader in mobile forensics. Their UFED solution allows forensic experts to extract logical, file system, and physical data from a wide range of mobile devices.
-
Logical Extraction: Access to standard user data (contacts, call logs, messages).
-
File System Extraction: Retrieves deleted files, app data, and hidden directories.
-
Physical Extraction: Accesses raw binary data from the memory chip. Ideal for recovering deleted data, even if the file system is corrupted.
Cellebrite supports advanced methods like JTAG, chip-off, and bootloader exploits to bypass locked devices and encrypted data.
2. Magnet AXIOM

Magnet AXIOM is another powerful forensic suite that can process and correlate data from mobile phones, cloud backups, and computers. It has a user-friendly interface and supports over 1,000 third-party mobile apps, which is crucial in cases involving social media, messaging platforms, and cloud syncs.
3. XRY by MSAB

MSAB’s XRY offers data extraction and analysis capabilities across various mobile platforms. It’s known for its focus on law enforcement applications and has strong support for compliance and chain of custody.
4. Oxygen Forensics Detective

Oxygen is widely used for parsing encrypted backups and unlocking app-level encryption. It’s especially valuable for dealing with WhatsApp, Telegram, Signal, and other secure communication apps.
The Challenge of Deleted Data
The idea that data is permanently lost once it is erased is among the most widespread misconceptions. In actuality, erased data could continue to exist in the device’s memory, frequently until it is replaced by fresh data. This is particularly true for application data, call logs, messages, and images.
However, sophisticated tools and methods are needed to recover this data. The success of recovery is influenced by the device type, operating system (iOS or Android), version, encryption level, and whether a factory reset was carried out.
Real-World Case Examples
The Bois Locker Room Case (2020)

Case: A private Instagram and WhatsApp group where Delhi schoolboys shared morphed photos of underage girls.
Forensic Breakthrough:
- Delhi Police’s cyber cell recovered deleted group chats and images from participants’ phones.
- Metadata analysis confirmed the origin of shared photos.
- IP tracing helped identify anonymous members
Outcome: Several minors were questioned, and the case highlighted the need for better cyber safety laws.
Pulwama Terror Attack (2019)

Category: National Security / Terrorism
Agency Involved: National Investigation Agency (NIA)
Background:
On 14 February 2019, a suicide bomber attacked a CRPF convoy in Pulwama, Jammu and Kashmir, killing 40 soldiers. The attack was claimed by the terror group Jaish-e-Mohammed (JeM).
Mobile Forensics In Action:
Damaged Device Recovery:
-
Investigators recovered severely damaged mobile phones from the car used in the blast and surrounding areas.
-
These phones were forensically examined using chip-off techniques and JTAG, since the devices were physically destroyed.
Data Extraction & Link Analysis:
-
Despite the damage, the NIA recovered deleted WhatsApp chats, videos, and call logs.
-
These digital artifacts included a “confession video” recorded by the suicide bomber Adil Ahmad Dar before the attack and sent to handlers in Pakistan via WhatsApp.
-
The metadata and cloud sync logs helped trace communication with JeM commanders based outside India.
Application of Cellebrite UFED and Magnet AXIOM:
Impact:
-
The evidence was admissible in court and helped the NIA file a detailed charge sheet.
-
Mobile forensic findings were crucial in identifying local accomplices, cross-border handlers, and funding channels.
Nirav Modi PNB Scam (₹11,000+ Crores Fraud, 2018)

Category: White Collar / Financial Crime
Agency Involved: Enforcement Directorate (ED), CBI
Background:
Nirav Modi, a billionaire jeweller, was accused of defrauding Punjab National Bank (PNB) through fraudulent Letters of Undertaking (LoUs) worth over ₹11,000 crores. He fled India before the scam surfaced.
Mobile Forensics In Action:
Deleted Messaging Recovery:
-
During raids, mobile phones and laptops belonging to Nirav Modi and his aides were seized.
-
Forensic examiners used Oxygen Forensics and Cellebrite to recover deleted emails, encrypted WhatsApp chats, and VoIP call records that were not available via normal backup.
Encrypted App Logs:
-
Investigators discovered that secure messaging apps like Signal and Wickr were used to communicate sensitive instructions and coordinate fraudulent LoUs.
-
Some of these were deleted, but forensic analysis recovered partial log files and metadata from app directories.
Cloud Token Extraction:
-
Cloud sync tokens were extracted from devices to access Gmail, Google Drive, and Apple iCloud accounts, revealing invoices, transaction histories, and instructions to employees.
Impact:
-
The recovered data helped in asset tracing, identifying money laundering routes, and co-conspirators across borders.
-
This digital evidence played a key role in Nirav Modi’s extradition proceedings in the UK.













Admin on July 16, 2025
Its good