Hashing techniques are vital to protecting sensitive data in the fields of cryptography and data security. Two of the most well-known hashing algorithms are the MD5 (Message Digest Algorithm 5) and SHA (Secure Hash Algorithm) families. Still, the topic of which is more secure comes up frequently. Let’s delve deeper into MD5 and SHA in more detail, examining their inner workings, vulnerabilities, and general security to determine which is more durable to modern threats.
Understanding MD5 and SHA
MD5 (Message Digest Algorithm 5)
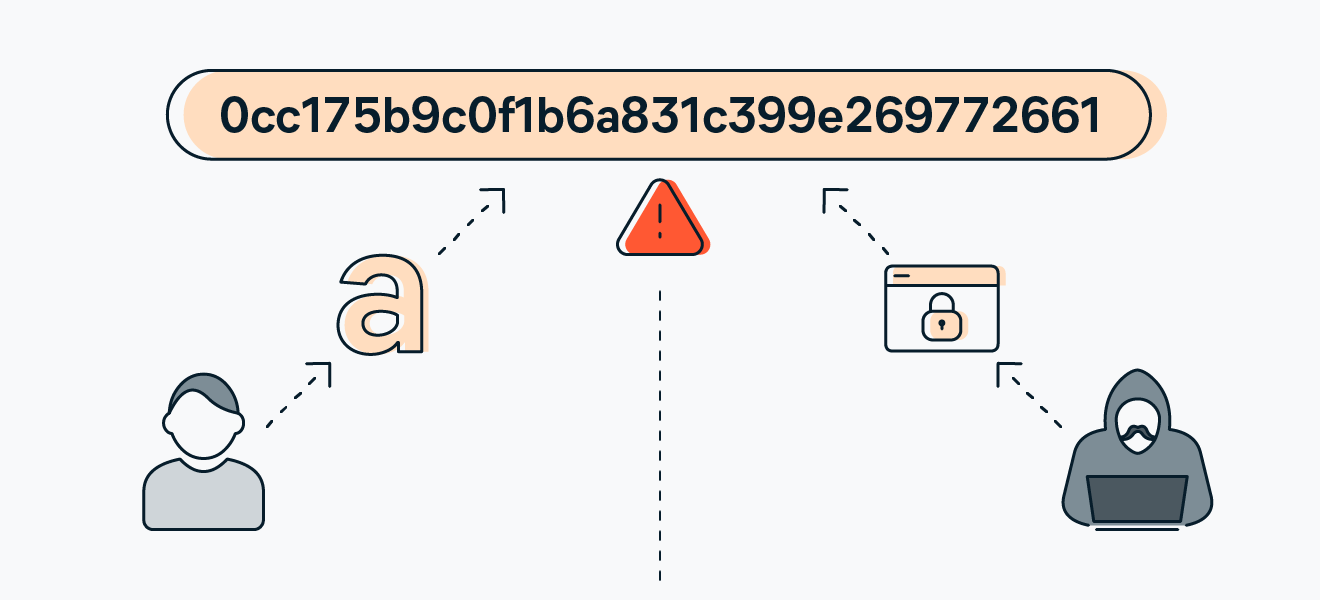
MD5, designed by Ronald Rivest in 1991, was once widely used for its speed and efficiency in generating fixed-size 128-bit hash values from variable-length inputs. But over time, flaws were found that made it unfit for use in cryptography because of its vulnerability to collision attacks.
Secure Hash Algorithm, or SHA
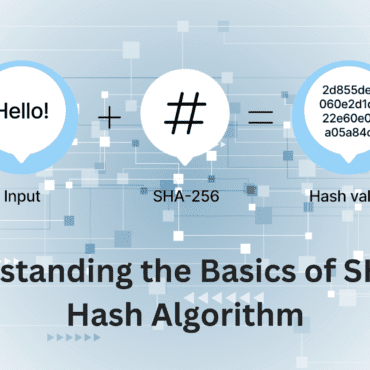
The National Security Agency (NSA) developed the SHA family, which includes several versions like SHA-1, SHA-2, and SHA-3. Of these, SHA-2 (which includes SHA-256, SHA-384, and SHA-512) and SHA-3 are still safe options for cryptographic applications, while SHA-1 has been deprecated because of security flaws. These algorithms produce hashes with varying bit lengths (SHA-256, for example, generates hashes with 256 bits).
Security Analysis: MD5 vs. SHA
Let’s compare now the two algorithms side by side.
Output size
The output of the MD5 algorithm is 128 bits, or 32 characters in hexadecimal.
The SHA-256 method uses 64 hexadecimal characters for every 256 bits, making it twice as long.
MD5 vs SHA-256: Which is faster?
The quickest cryptographic algorithm is MD5. SHA-256 performs 20% less quickly.
You can use MD5 going forward if speed is your primary concern.
Comparing SHA-256 and MD5, which is more secure?
While not flawless, SHA-256 is marginally more secure than MD5. It generates a hash that is 256 bits large, double that of MD5. Also, SHA-256 has a lower collision probability than MD5.
If security is your main criteria, and you have only these two options, SHA-256 would be better. But don’t forget that no algorithm is 100% safe.
Which is better, SHA-256 or MD5?
Use SHA-256 instead of MD5 wherever possible. Since SHA-256 is slower than MD5 and produces a value of 256 bits as opposed to MD5’s 128 bits, SHA-256 is usually better than MD5.
Even though SHA-256 isn’t ideal, it’s still preferable when used for purposes other than hashing because it doesn’t really matter if it’s slightly slower.
Current Usage and Recommendations
It is no longer advised to use MD5 for cryptography due to its vulnerabilities. Rather, because of their resilience to attacks, SHA-2 (particularly SHA-256) and SHA-3 are widely utilized in digital signatures, blockchain technology, SSL certificates, and other security protocols.
Conclusion
The SHA family has a clear advantage in the conflict between MD5 and SHA. Although MD5’s speed initially made it recognized, its vulnerability to attacks—particularly collision attacks—makes it unreliable for use in cryptography. However, SHA algorithms—especially the SHA-2 and SHA-3 variants—offer better protection against known flaws and are frequently used in modern security applications to ensure data integrity and confidentiality.
Essentially, choosing SHA algorithms over MD5 is essential when security and dependability are your top priorities in order to protect sensitive data from ever changing cyber threats.
Remember that even though SHA is currently secure, continuous research and development are needed to stay ahead of possible vulnerabilities in the future. As a result, when security standards evolve to deal with new threats, it is recommended that you upgrade frequently and switch to hashing algorithms with greater strength.


Post comments (0)